Add Backtrack Tools Into Ubuntu11.04
Updated: 2011-09-30 01:16:00
 IT professionals have accepted there are positive benefits to using social media, but they lack the tools necessary to protect enterprises from cyber-threats that enter through social networking sites. - IT professionals consider social media as a positive business tool
within the enterprise, but they were concerned they didn't have the
right technology and policies to deal with the dangers, a recent report
found.
The quot;Global Survey on Social Media Risks quot; from the Ponemon Institu...
IT professionals have accepted there are positive benefits to using social media, but they lack the tools necessary to protect enterprises from cyber-threats that enter through social networking sites. - IT professionals consider social media as a positive business tool
within the enterprise, but they were concerned they didn't have the
right technology and policies to deal with the dangers, a recent report
found.
The quot;Global Survey on Social Media Risks quot; from the Ponemon Institu... A Verizon Business report found that organizations that have been validated as being PCI-DSS compliant are no longer meeting standards a year later. - Retailers
and merchants are still falling short of payment card security requirements,
according to a new report.
The
latest Payment Card Industry Compliance Report found that a majority of small
businesses in the United States, Europe and Asia have fallen short of
maintaining compliance with ...
A Verizon Business report found that organizations that have been validated as being PCI-DSS compliant are no longer meeting standards a year later. - Retailers
and merchants are still falling short of payment card security requirements,
according to a new report.
The
latest Payment Card Industry Compliance Report found that a majority of small
businesses in the United States, Europe and Asia have fallen short of
maintaining compliance with ... Mozilla fixed a handful of critical vulnerabilities in Firefox 7 and Thunderbird 3.15. Users should be sure to download it from the actual Mozilla site and not get scammed. - Mozilla fixed eight known security flaws in the latest
version of the popular Firefox Web browser. Mozilla also fixed a cross-site
scripting bug in Firefox 6, six weeks after its release.
Firefox 7, released Sept. 27, contains fixes for six
quot;critical quot; and two quot;moderate quot; vuln...
Mozilla fixed a handful of critical vulnerabilities in Firefox 7 and Thunderbird 3.15. Users should be sure to download it from the actual Mozilla site and not get scammed. - Mozilla fixed eight known security flaws in the latest
version of the popular Firefox Web browser. Mozilla also fixed a cross-site
scripting bug in Firefox 6, six weeks after its release.
Firefox 7, released Sept. 27, contains fixes for six
quot;critical quot; and two quot;moderate quot; vuln... Microsoft obtained a court order to block the command and control servers held by the Kelihos botnet, also known as Waldedac 2.0 before it could grow and become more disruptive. - Days after wrapping up its civil case against the Rustock
botnet, Microsoft is back in court, this time to shut down the Kelihos network.
Using the same
technique that had worked so well in its previous campaigns against the Rustock
and Waledac, Microsoft asked the United States District Court...
Microsoft obtained a court order to block the command and control servers held by the Kelihos botnet, also known as Waldedac 2.0 before it could grow and become more disruptive. - Days after wrapping up its civil case against the Rustock
botnet, Microsoft is back in court, this time to shut down the Kelihos network.
Using the same
technique that had worked so well in its previous campaigns against the Rustock
and Waledac, Microsoft asked the United States District Court... In this article the author will review some of the tips, concepts, tools, and overall approaches in determining the root cause of log events.
In this article the author will review some of the tips, concepts, tools, and overall approaches in determining the root cause of log events. The Pentagon is considering the pilot program in which it shares classified threat intelligence with the private sector a success and will extend it to November. - The Department of Defense is planning
to extend the cyber-defense pilot program in which it shares classified threat
intelligence with defense contractors and other companies.
The Defense Industrial Base Cyber-Pilot
provides member organizations with classified information about viruses,
malwar...
The Pentagon is considering the pilot program in which it shares classified threat intelligence with the private sector a success and will extend it to November. - The Department of Defense is planning
to extend the cyber-defense pilot program in which it shares classified threat
intelligence with defense contractors and other companies.
The Defense Industrial Base Cyber-Pilot
provides member organizations with classified information about viruses,
malwar... Spammers are finding it more lucrative to compromise email marketing firms and exploit their resources to send out malicious messages. - Attackers are
increasingly targeting email marketing firms and corporate email accounts to
power their spam campaigns, Websense Security researchers reported.
Websense
Security Labs has observed a rise in spam being sent from corporate Webmail
accounts, wrote David Saunders, email threat resear...
Spammers are finding it more lucrative to compromise email marketing firms and exploit their resources to send out malicious messages. - Attackers are
increasingly targeting email marketing firms and corporate email accounts to
power their spam campaigns, Websense Security researchers reported.
Websense
Security Labs has observed a rise in spam being sent from corporate Webmail
accounts, wrote David Saunders, email threat resear... While the Senate Judiciary Committee approved three data breach and privacy bills, it's still unclear whether a federal data breach notification law will pass this year. - The Senate Judiciary Committee approved three data security
and privacy bills over strong objections from Republican members last week. The
opposition may complicate efforts to pass comprehensive cyber-security
legislation this year, observers said.
Committee members voted along party lines, 10 ...
While the Senate Judiciary Committee approved three data breach and privacy bills, it's still unclear whether a federal data breach notification law will pass this year. - The Senate Judiciary Committee approved three data security
and privacy bills over strong objections from Republican members last week. The
opposition may complicate efforts to pass comprehensive cyber-security
legislation this year, observers said.
Committee members voted along party lines, 10 ... Third-party client side exploits continue to be a favored attack vector especially in widely deployed tools like Adobe Reader and Internet browsers. Recent studies show that third-party programs are responsible for 69% of the vulnerabilities on a typical endpoint. Unfortunately, for many smaller companies the process of identifying these vulnerabilities and then efficiently patching them [...]
Third-party client side exploits continue to be a favored attack vector especially in widely deployed tools like Adobe Reader and Internet browsers. Recent studies show that third-party programs are responsible for 69% of the vulnerabilities on a typical endpoint. Unfortunately, for many smaller companies the process of identifying these vulnerabilities and then efficiently patching them [...] BoxTone enhances its mobile device management platform with automated security policy, compliance management capabilities and Active Directory integration. - BoxTone
has added automated compliance management capabilities to its mobile device
management software.
The
Enterprise Mobile Management platform has been updated to include a fully
automated policy and compliance management engine, a real-time mobile security
dashboard, analytics, alerting a...
BoxTone enhances its mobile device management platform with automated security policy, compliance management capabilities and Active Directory integration. - BoxTone
has added automated compliance management capabilities to its mobile device
management software.
The
Enterprise Mobile Management platform has been updated to include a fully
automated policy and compliance management engine, a real-time mobile security
dashboard, analytics, alerting a... Cyber-criminals injected JavaScript code to divert visitors from MySQL.com to a malicious site hosting BlackHole malware toolkit in a drive-by-download attack. - Unknown attackers compromised the main Website of open-source
database MySQL and served malware to unsuspecting visitors for a short
period of time on Sept. 26.
Attackers injected JavaScript code on MySQL.com, owned by
Oracle, to divert visitors to malicious Websites hosting the BlackHole exploi...
Cyber-criminals injected JavaScript code to divert visitors from MySQL.com to a malicious site hosting BlackHole malware toolkit in a drive-by-download attack. - Unknown attackers compromised the main Website of open-source
database MySQL and served malware to unsuspecting visitors for a short
period of time on Sept. 26.
Attackers injected JavaScript code on MySQL.com, owned by
Oracle, to divert visitors to malicious Websites hosting the BlackHole exploi... The U.S. departments of Homeland Security and Commerce have issued a request for proposal to develop a program which would have major ISPs detect and notify customers they are part of a bot army. - Homeland Security and Commerce departments are considering a
voluntary program in which Internet service providers will proactively detect
infected computers participating in a botnet.
The Department of Homeland Security, National
Telecommunications and Information Administration and the Nationa...
The U.S. departments of Homeland Security and Commerce have issued a request for proposal to develop a program which would have major ISPs detect and notify customers they are part of a bot army. - Homeland Security and Commerce departments are considering a
voluntary program in which Internet service providers will proactively detect
infected computers participating in a botnet.
The Department of Homeland Security, National
Telecommunications and Information Administration and the Nationa... Microsoft's Windows 8 security measures include secure boot. As demonstrated at BUILD, this means compromised systems can refuse to boot. - Microsoft is detailing some of its
security procedures for Windows 8.
Key to Windows 8s platform integrity
architecture is its Unified Extensible Firmware Interface (UEFI), a set of
specifications for how the operating system communicates with platform firmware
during the boot-up process. UE...
Microsoft's Windows 8 security measures include secure boot. As demonstrated at BUILD, this means compromised systems can refuse to boot. - Microsoft is detailing some of its
security procedures for Windows 8.
Key to Windows 8s platform integrity
architecture is its Unified Extensible Firmware Interface (UEFI), a set of
specifications for how the operating system communicates with platform firmware
during the boot-up process. UE... Facebook's Timeline user interface is raising eyebrows and heart rates from media and pundits who fear the social network is becoming a little too revealing. - Google's (NASDAQ:GOOG) Executive
Chairman Eric Schmidt took a lot of flak from the media for a comment he made at
an event at the Newseum in Washington, D.C., last October.
Schmidt,
responding to a question about the possibility of Google developing some kind
of neurological implant, replied: ...
Facebook's Timeline user interface is raising eyebrows and heart rates from media and pundits who fear the social network is becoming a little too revealing. - Google's (NASDAQ:GOOG) Executive
Chairman Eric Schmidt took a lot of flak from the media for a comment he made at
an event at the Newseum in Washington, D.C., last October.
Schmidt,
responding to a question about the possibility of Google developing some kind
of neurological implant, replied: ... A recap of the past week's IT security news includes multiple spear phishing attacks, arrests of suspected Anonymous and LulzSec members and concerns about SSL security. - Major Spear phishing attacks continued to make headlines in the past week. Japan's largest defense contractor, Mitsubishi Heavy Industries, disclosed it had discovered more than 80 servers and computers had been infected with several types of malware in its headquarters, manufacturing plants and shi...
A recap of the past week's IT security news includes multiple spear phishing attacks, arrests of suspected Anonymous and LulzSec members and concerns about SSL security. - Major Spear phishing attacks continued to make headlines in the past week. Japan's largest defense contractor, Mitsubishi Heavy Industries, disclosed it had discovered more than 80 servers and computers had been infected with several types of malware in its headquarters, manufacturing plants and shi... Wave Systems acquired Safend, a provider of endpoint data loss prevention, including port and device control, encryption for removable media, content inspection and discovery. - Wave Systems has acquired Israeli company Safend for
approximately $12.8 million to expand its portfolio of security and encryption
products.
The Cupertino Calif-based paid $1.1 million in cash and 5.2
million shares of Wave Systems common stock, valued at $2.214 per share to
close the deal, W...
Wave Systems acquired Safend, a provider of endpoint data loss prevention, including port and device control, encryption for removable media, content inspection and discovery. - Wave Systems has acquired Israeli company Safend for
approximately $12.8 million to expand its portfolio of security and encryption
products.
The Cupertino Calif-based paid $1.1 million in cash and 5.2
million shares of Wave Systems common stock, valued at $2.214 per share to
close the deal, W... SSL is under attack once again, as this time two researchers claim to have come up with an attack tool, dubbed BEAST, that can crack SSL traffic used to secure Websites - Security researchers are set to unveil the attack tool
capable of breaking the encryption algorithm that protects Websites. Hours
before the presentation, cryptography experts provided recommendations on how
to defend Websites from the exploit.
Researchers Thai Duong and Juliano Rizzo are schedu...
SSL is under attack once again, as this time two researchers claim to have come up with an attack tool, dubbed BEAST, that can crack SSL traffic used to secure Websites - Security researchers are set to unveil the attack tool
capable of breaking the encryption algorithm that protects Websites. Hours
before the presentation, cryptography experts provided recommendations on how
to defend Websites from the exploit.
Researchers Thai Duong and Juliano Rizzo are schedu...
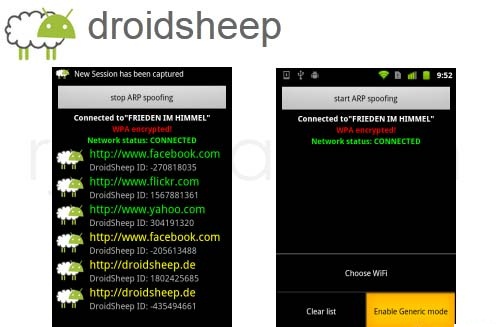
 Software is written by people and inevitably has mistakes and requires maintenance. This maintenance can be in the form of security updates to patch vulnerabilities, service packs and hot fixes to correct functional problems, and general maintenance to cover required updates for signatures and other time-dependent functions. When working with security solutions, detection methods often [...]
Software is written by people and inevitably has mistakes and requires maintenance. This maintenance can be in the form of security updates to patch vulnerabilities, service packs and hot fixes to correct functional problems, and general maintenance to cover required updates for signatures and other time-dependent functions. When working with security solutions, detection methods often [...] Earlier today, George Hulme reported on a recently-introduced piece of legislation, the Personal Data Protection and Breach Accountability Act of 2011 (or PDPBAA for short, which sounds like how my last is pronounced sometimes), geared toward protecting customer data from theft or loss. Senator Richard Blumenthal (D-CT) hopes that this new bill will “prevent and [...]
Earlier today, George Hulme reported on a recently-introduced piece of legislation, the Personal Data Protection and Breach Accountability Act of 2011 (or PDPBAA for short, which sounds like how my last is pronounced sometimes), geared toward protecting customer data from theft or loss. Senator Richard Blumenthal (D-CT) hopes that this new bill will “prevent and [...] Quite unsurprisingly (as they accidentally leaked them last Friday), Microsoft released 5 security bulletins today. This month is fairly moderate, with none of the bulletins rating a critical rating. Included in the bulletins is the second update to WINS this year (MS11-070). As a reminder, if you are running WINS and you can’t really remember [...]
Quite unsurprisingly (as they accidentally leaked them last Friday), Microsoft released 5 security bulletins today. This month is fairly moderate, with none of the bulletins rating a critical rating. Included in the bulletins is the second update to WINS this year (MS11-070). As a reminder, if you are running WINS and you can’t really remember [...] Today I have a guest commentary on the changes in security landscape since 2001 in Threatpost. So as I look back over the last 10 years I don’t see much of a change in the vulnerability-scape, if you will, but in the threat landscape. New classes of attackers have gone mainstream and global. They are [...]
Today I have a guest commentary on the changes in security landscape since 2001 in Threatpost. So as I look back over the last 10 years I don’t see much of a change in the vulnerability-scape, if you will, but in the threat landscape. New classes of attackers have gone mainstream and global. They are [...] One of the most important facets regarding security is escalating data to the proper individuals in a timely manner. This is generally done using reports or some form of email alerts. In the context of reports, securing and proper distribution of the contents is just as important as the data contained within. In other words, [...]
One of the most important facets regarding security is escalating data to the proper individuals in a timely manner. This is generally done using reports or some form of email alerts. In the context of reports, securing and proper distribution of the contents is just as important as the data contained within. In other words, [...] In this article the author discusses the following Microsoft security tools - MBSA, Security templates, SCW and SCM.
In this article the author discusses the following Microsoft security tools - MBSA, Security templates, SCW and SCM.  At the recent BlackHat and DefCon conferences, our annual eEye Research Team T-shirt was one of the more memorable ones we’d done in a while (and if you remember 2005, that’s saying something). In keeping with the theme of Security in Context, the shirt parodied the fear that attacks like Stuxnet, NightDragon and Operation Aurora had [...]
At the recent BlackHat and DefCon conferences, our annual eEye Research Team T-shirt was one of the more memorable ones we’d done in a while (and if you remember 2005, that’s saying something). In keeping with the theme of Security in Context, the shirt parodied the fear that attacks like Stuxnet, NightDragon and Operation Aurora had [...]